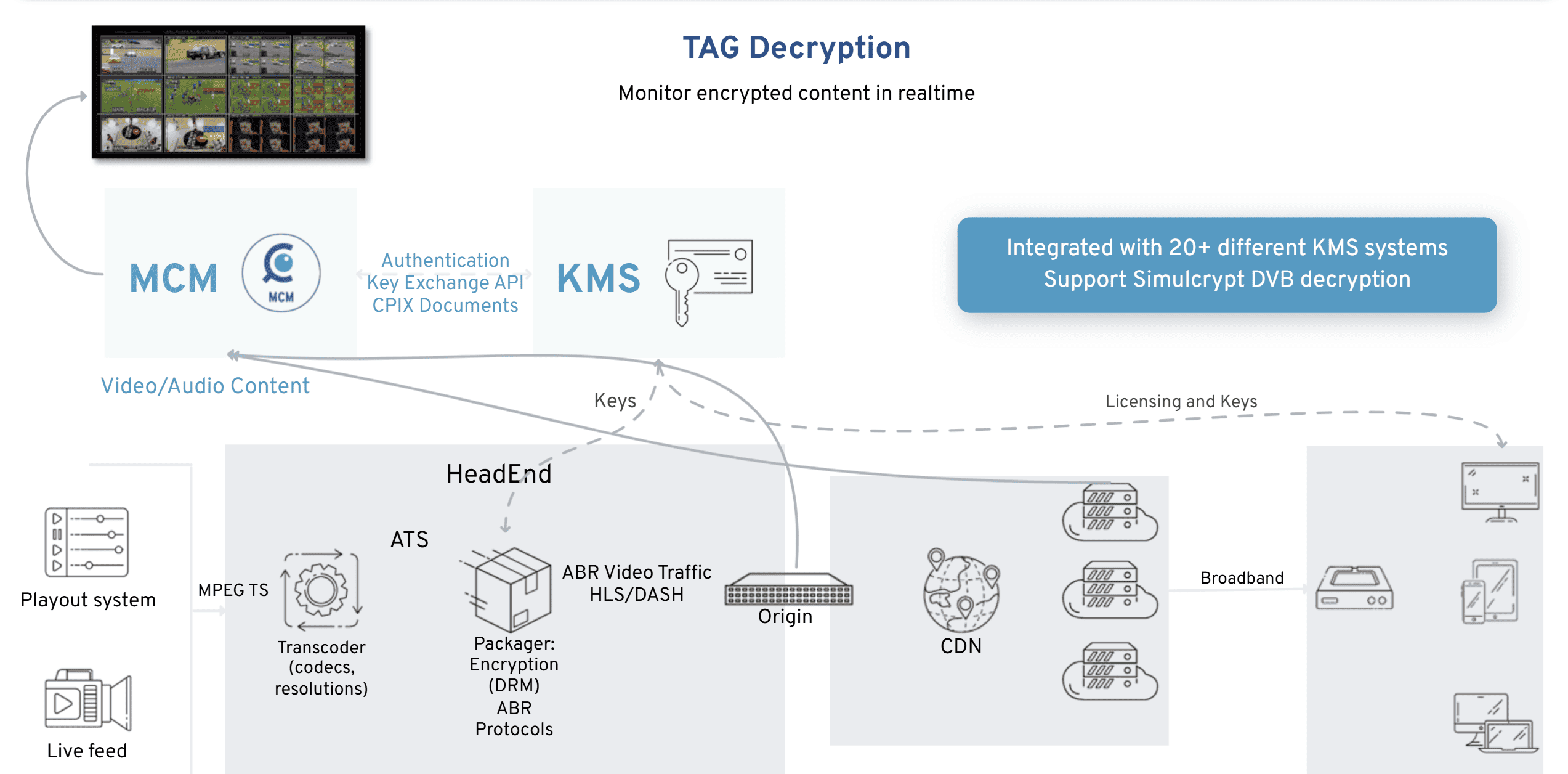
TAG’s Decryption feature enables secure, scalable, and efficient handling of encrypted video streams by integrating directly with leading Key Management Systems (KMS). Supporting standards such as AES-128 (CBC/CTR), BISS-2, CENC for multi-DRM, and DVB Simulcrypt, it allows operators to monitor both live and VOD content across broadcast, IPTV, and OTT environments.
By connecting with KMS partners including Verimatrix, Irdeto, Huawei PlayReady, Axinom, and others, Decryption ensures seamless key exchange and removes the need for additional DRM infrastructure. This simplifies workflows while maintaining security and compliance.
The system scales easily across on-premises, cloud, and hybrid deployments, delivering high-throughput decryption with minimal overhead. Operators gain the ability to probe encrypted streams in real time, ensuring fault detection, regulatory compliance, and service reliability without adding costly hardware.
Decryption empowers broadcasters, operators, and content providers to maintain full visibility into protected content, reduce operational friction, and ensure both revenue protection and viewer trust.
Decryption Specifications
- AES-128 (CBC, CTR)
- BISS-2 Encryption
- Common Encryption (CENC) for Multi-DRM
- DVB Simulcrypt Support (ECM, EMM-based CA Systems)
- Verimatrix, Irdeto, SKY CKS, Huawei PlayReady, Axinom, buyDRM, Kaltura UDRM, and others.
- CPIX support for secure, dynamic key exchange.